Five ways to help you build trust with your third parties
- David Walker

- May 5, 2020
- 5 min read
The results of our third-party risk management (TPRM) survey are timely with increased dependence on third parties in the COVID-19 pandemic.
The rapidly evolving threat around the COVID-19 virus is raising concerns about the resilience of enterprises globally. One potentially overlooked vulnerability? The increasing dependence on third parties. The interconnectedness of today’s business environment and the use of external vendors – from supply chains to the delivery of critical business services – poses a risk of disruption that can result in significant revenue loss.
The Pallas Consultants TPRM survey covers a broad range of organizations, including advanced manufacturing and mobility, financial services, banking and capital markets, consumer, health, insurance, life sciences, power and utilities, technology, media and entertainment, and telecommunications.
The results, examined in this article, identify some notable trends in the following five areas:
1. Operating model and governance
2. Automation, technology and reporting
3. Fourth parties, data breaches and resiliency
4. Risk expansion and frameworks
5. Emerging focus areas
These trends include a gradual movement toward centralization of risk in parallel with increased use of consortia/market utilities to expand the coverage and depth of due diligence. While technologies such as artificial intelligence (AI) are increasing in use, organizations should define their own specific reporting framework and requirements before automating risk-related processes.
There are also heightened expectations from stakeholders and a growing awareness of the risks presented by entering new ventures and markets with respect to partners, joint ventures, collaborators, fourth parties and other relationship structures. These fourth parties remain a blind spot for the vast majority of organizations.
Chapter 1 Operating model and governance
Still no consensus around ownership of TPRM programs, but a gradual move toward centralization.
There is still no consensus in the industry around the ownership of TPRM programs. However, we are seeing a continued gradual movement toward centralization.
There are numerous reasons for this: the need to consider various risk lenses (for example, privacy, fourth-party risk, resiliency) in a consistent manner; having an end-to-end transparent view into the third-party engagement life cycle; a clear delineation of responsibility and accountability across the lines of defense; and making adherence to policies and standards more rigorous and consistent.
There is also pressure to deliver due diligence outcomes faster, across a broader and deeper scope. To do this, organizations are turning to market utilities more often to decrease cycle times and increase the quality of data going into due diligence and ongoing oversight decisions. At the same time, organizations are shifting the internal headcount that traditionally supported these functions to more value-adding risk management activities, and engaging external parties to handle the variable nature of assessment volumes.

Chapter 2 Automation, technology and reporting
Integrating technology across TPRM ecosystems is increasing, but tech-based tools not a cure-all.
Over the last few years, organizations have moved toward streamlining and integrating technology and various tool sets across the third-party management ecosystem.
Clients have shown interest and have started conversations about leveraging advanced analytics and AI to demonstrate the value of TPRM programs, find opportunities to manage costs, and identify better insights in data to respond to complex new regulatory requirements. However, only one in five organizations surveyed are currently using advanced analytics. Organizations are also seeking integration with consortia, market utilities and other management services.
However, tech-based tools are not a cure-all. Organizations should define reporting frameworks and requirements (key performance and risk indicators) that are fit for purpose and unique to the organization before enabling them through technology. As organizations leverage technology and automation, they have an opportunity to gather more data across many processes to improve reporting, TPRM and procurement processes and analytics.

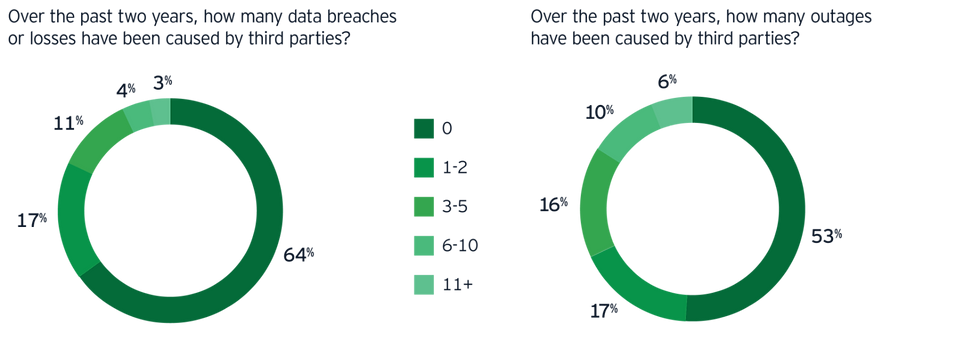
Chapter 3 Fourth parties, data breaches and resiliency
Fourth-party reviews should be higher on the risk management agenda.
Fourth parties remain a blind spot for many organizations. Relatively few organizations perform their own independent reviews of fourth parties and are increasingly relying on contractual terms between the third and fourth-party for oversight.
Fourth-party reviews should be higher on the risk management agenda as they can present a blind spot for various third-party risks to the organization. The organization, as data owners, will ultimately be held accountable for any nth (fourth, fifth, sixth) party breach. The organization must always know where their data is going, especially customer data, how it is being handled or used and who is accessing and/or using the data.
Organizations can reduce their potential exposure by evaluating risks up front and considering fourth parties within the inherent risk assessment at the initial contracting, on-boarding phase or within ongoing oversight activities. They could also leverage automated threat intelligence tools for more insightful reviews of fourth parties; this is an approach that the majority of survey respondents do not use today.
Chapter 4 Risk expansion and frameworks
Organizations are looking to leverage external data sources for their risk expansion.
The organizations surveyed generally rely on standardized frameworks as a baseline for their risk assessment questionnaires, though the specific frameworks they use vary widely.
Reassessment (risk/control assessment) 76%
of organizations reassess critical third parties on an annual basis.
Frameworks for other risk lenses are newly developed (for example, General Data Privacy Regulation and California Consumer Privacy Act) or may not exist at all, as organizations do not have a reference point on what others are using to address these risks. This may be why more organizations are looking to leverage external data sources to understand and evaluate their risk expansion and to better align their TPRM methodology.
Risk expansions of regulatory compliance and operational risks are prevalent. Some organizations are actually weighing the cost and effort of compliance against the likelihood of enforcement actions against them.
If a company is expanding, only limited frameworks are available to allow for simultaneous assessment of third parties in cybersecurity and privacy, as well as the other risk expansion areas like resiliency.
Chapter 5 Emerging focus areas
Enhanced focus on areas such as cybersecurity, supply chain and defining critical relationships.
Organizations are faced with heightened expectations from risk management stakeholders, as well as entry into new ventures and markets, which carry their own risks.
There has also been enhanced focus and dialogue in other areas, including cybersecurity, fourth-party and supply chain risk, and global coverage and applicability of regulations.
Additionally, there is a growing focus on the definition of critical relationships, especially at the board level. While the demand for oversight of TPRM programs increases, there is also more integration of TPRM with Operational Risk and Enterprise Risk Management programs to provide a composite view to management.Organizations have a desire for more board involvement, but at the moment, the reality is quite different.
Summary
Our third-party risk management (TPRM) survey identifies five areas that organizations are focusing on to build trust with third parties in a technology-driven and disrupted world. These include a gradual movement toward centralization of risk, and an increasing use of technologies such as artificial intelligence.


